Видео с ютуба Cryptography (Algorithm Family)

The SPEEDY Family of Block Ciphers: Engineering an Ultra Low-Latency Cipher from Gate Level for...

7 Cryptography Concepts EVERY Developer Should Know

The PHOTON Family of Lightweight Hash Functions (Crypto 2011)

The RSA Encryption Algorithm (1 of 2: Computing an Example)

BLAKE3 and bao deep dive

Observations on the SIMON Block Cipher Family
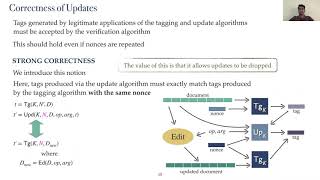
Incremental Cryptography Revisited: PRFs,Nonces and Modular Design

Family Called Me Jobless — Then My Name Appeared On Fortune's Cover, Everything Changed...

The SKINNY Family of Lightweight Tweakable Block Ciphers

Beetle Family of Lightweight and Secure Authenticated Encryption Ciphers

Cryptanalysis of the FLIP Family of Stream Ciphers

Feistel Cipher - Computerphile

Duel of the Titans: The Romulus and Remus Families of Lightweight AEAD Algorithms

PRFs explained: Transforming Secrets into Infinite Keys - Pseudo Random Functions

On families of stream ciphers based on the approximations of regular forests, Pustovit Oleksandr

How the MD5 hash function works (from scratch)

Post quantum cryptography in automotive

Pseudorandom function family

AES Explained (Advanced Encryption Standard) - Computerphile

What Is The SHA Family? - SecurityFirstCorp.com